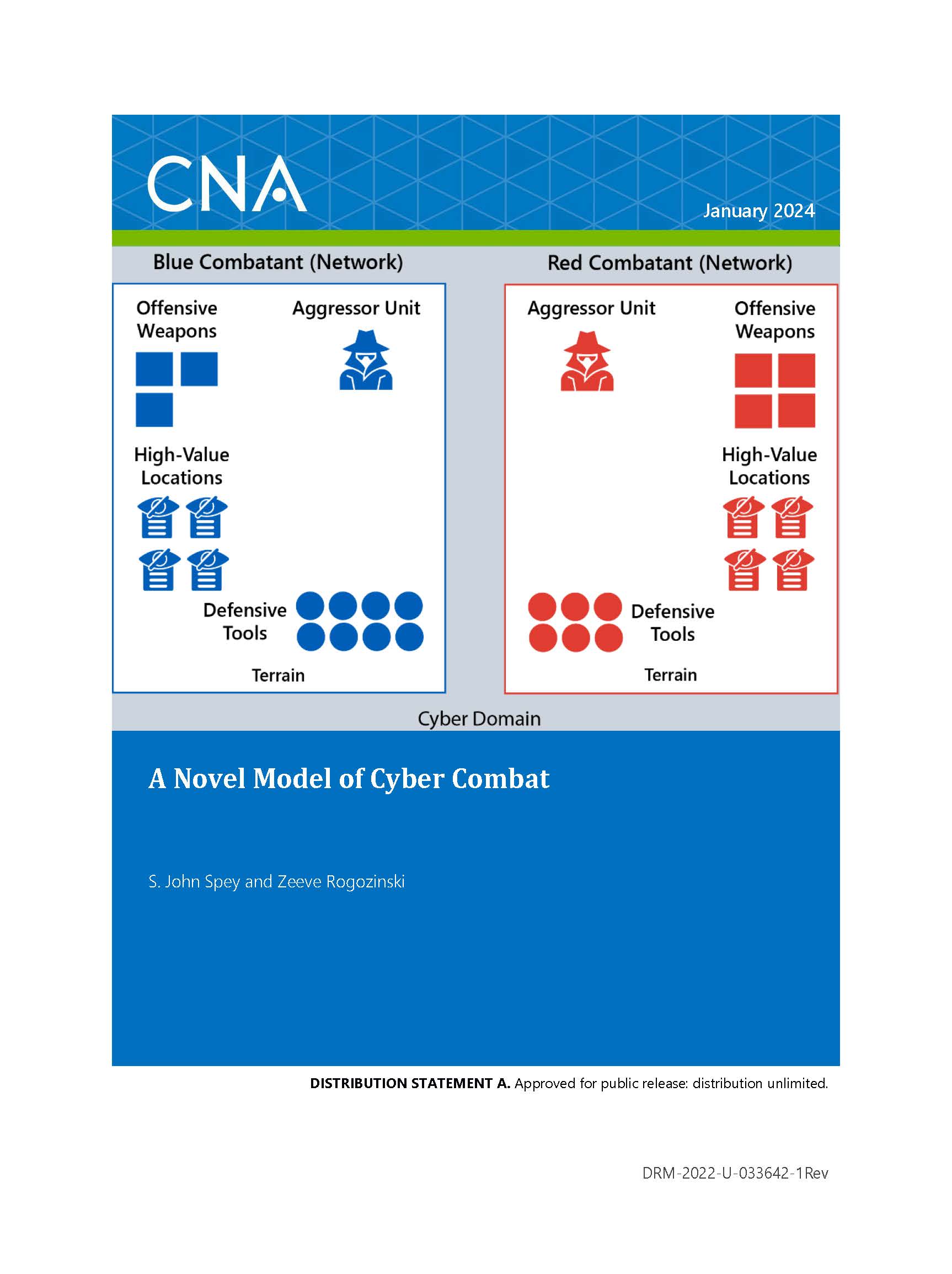
As part of a CNA-initiated, Navy-funded effort, we have developed a computer-based model of cyber combat at the high-tactical level or operational level. The model is designed to allow experimentation with longer term strategies across multiple attempted or successful network intrusions, so it has a high level of abstraction. Instead of modeling specific offensive weapons and defensive tools, it uses single values to summarize their effectiveness. Those values then determine the probabilities of potential outcomes of interactions between model participants.
A more specific example of the abstract nature of the model is that the progress of aggressors moving through target networks is modeled as a countdown timer that the aggressor must wait through before reaching an objective rather than the model checking repeatedly for how much incremental progress that the aggressor makes. From the high-tactical perspective, what is of interest is whether the aggressor can reach its target location inside the target network before being detected and ejected from the network.
The simplistic nature of the model allows it to run a complete model simulation in a fraction of a second. The model iterates the same simulation many hundreds or thousands of times with the same initial conditions and strategies to create a distribution of outcomes. The initial conditions can then be changed before iterating the model another several hundred or thousand times. This approach allows the model to be used to explore new scenarios rapidly. If the code of the model is also modified to implement different force commander strategies, the model can be used to explore an even wider range of scenarios.
Model description
In its current state, the model runs with two or more sides, called combatants. Combatants attempt to gain illicit access into each other’s cyber terrain, seeking either to create effects in the cyber domain by neutralizing their enemy’s defensive tools or offensive weapons or to gain access to high-value locations inside the enemy’s network that provide benefits outside of the cyber domain. Because the model is only of the cyber domain, when aggressors reach locations that provide them with benefits outside cyber, the model rewards their combatant with abstract points. The model’s output includes a distribution of tools and weapons remaining on each side and the points each combatant scored.
Validation
We have partially validated the model by comparing the model’s results for how long network intrusions should last before they are detected with real-world data on the durations of network intrusions. Rather than directly simulating individual network intrusions, we analyzed both the model processes and real-world data to find the distribution of intrusion durations. We developed an underlying statistical model driving these distributions and found that both the model and real-world data predict the same distributions.
Insights
Using the model, we have also developed several insights about cyber combat via some simple explorations and analysis:
- For intrusions to last long enough for aggressors to accomplish any objectives, aggressors must be much better than defenders at the tactical level. If aggressors are not several orders of magnitude better at avoiding detection than defenders are at detecting them whenever the model tests for detection, network intrusions end very quickly.
- Assuming all defensive tools have an equal probability of detecting an aggressor inside the network, the marginal benefit from adding one more tool to the network decreases as a reciprocal of a root of the number of tools. This rapid decrease suggests improving the detection probability of existing tools rather than adding another tool equal in value to existing ones.
- All else being equal, the best strategy is to go after only objectives that provide benefits outside the cyber domain. It is a waste of effort for any aggressor units to go after the other goals of neutralizing the enemy’s tools or weapons that are not yet in use.
Approved for public release: distribution unlimited.
Details
- Pages: 40
- Document Number: DRM-2022-U-033642-1Rev
- Publication Date: 1/11/2024